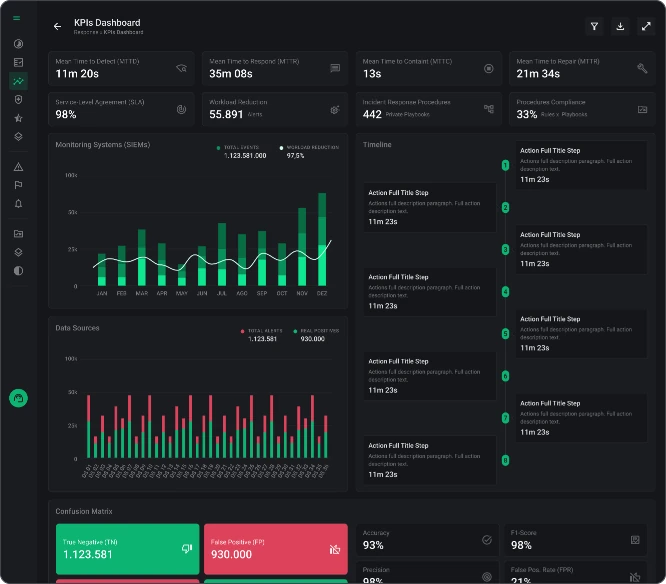
Mean time, number of incident response and Compliance
Explore critical SOC performance metrics like MTTD, MTTR, compliance rates, and more with the Inopli KPI Dashboard to gauge team efficacy and optimize incident management.
MTTD (Mean Time to Detect)
This is the average time it takes to detect a problem after it has occurred. A reduction in this time implies faster identification and response to incidents, minimizing potential damages.
MTTR (Mean Time to Respond)
This is the average time it takes to respond to an incident after it has been detected. A shorter MTTR indicates a more agile and prepared team to handle incidents.
MTTC (Mean Time to Contain)
This is the average time to contain an incident once it has been identified. A reduction in this time limits the spread of damage.
MTTR (Mean Time to Repair)
This is the average time it takes to fix an issue after it has been contained. A reduction in this time can lead to quicker recovery and lesser service interruptions.
Number of Incident Response Playbooks
This is the total number of Incident Response Playbooks implemented in Documents Managements, reflecting the team's ability to handle a variety of situations.
Incident Response Playbooks Coverage
This indicator measures the percentage of Correlation Rules that have documented Incident Response Playbooks. A high percentage reflects thorough preparation and a more structured response system.
Compliance with SLA (Service Level Agreement)
This metric showcases the proportion of instances where the agreed-upon service levels were fulfilled. It plays a vital role not only in ensuring customer satisfaction but also in avoiding contractual issues.
Workload Reduction
This metric shows the amount of work saved through automation and other efficiencies.
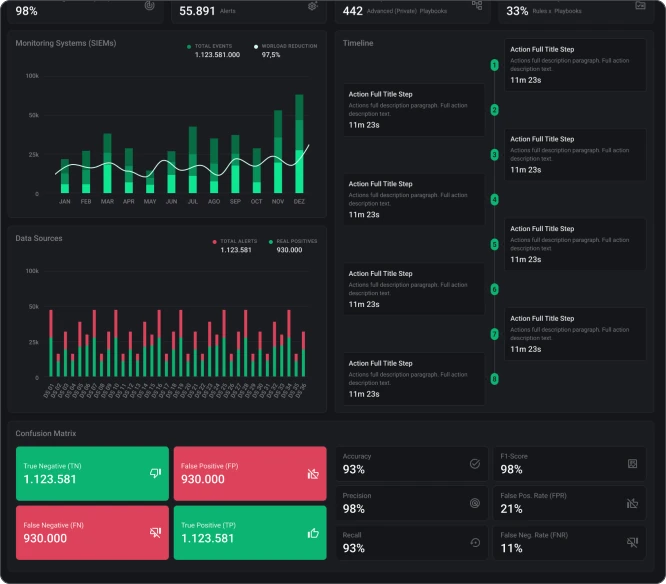
Qualitative evaluation: three stages system
For qualitative evaluation, Inopli has implemented a feedback system within Incident Management. This system tracks operational maturity progress via adaptable metrics, enabling leadership and senior cybersecurity staff to thoroughly assess team performance.
The assessment process is split into 3 stages for a thorough and fair evaluation.
False Positive Validation
This helps prevent irrelevant incidents from escalating to the customer.
Technical Proficiency
Responses should be rooted in specific cybersecurity knowledge and concepts, reinforcing the analysis results.
Security Recommendation
Every incident response should incorporate pertinent mitigation tactics and, if needed, additional resources for thorough comprehension.
Policy Compliance
Responses should conform to the team's guidelines, including writing style and other stipulated best practices.
Incident Follow-up
Essential for showing customers a committed, responsive team and for internal coordination, especially when customer analysts are involved.
Historical Analysis
For repeated cyber-attacks causing multiple incidents, reviewing past incidents within Inopli can help detect patterns and identify recurring threat actors.
Incident Response Rating
An incident response rating, ranging from 1 to 5 stars, is generated based on this evaluation. This rating serves as an immediate indicator of performance and response quality.
Quality Indicators Established Per Analyst
Inopli uses this data to establish quality indicators for each analyst's incident response. These indicators support ongoing, in-depth analysis of team effectiveness, help identify areas for improvement, and track progress over time.

